In the digital age, safeguarding your data and applications in the cloud is not just a priority; it’s a necessity. An effective Cloud Security Strategy is your shield against the evolving landscape of cyber threats and data vulnerabilities. We offer comprehensive Cloud Security Strategy Services to help you fortify your cloud infrastructure and protect your digital assets.
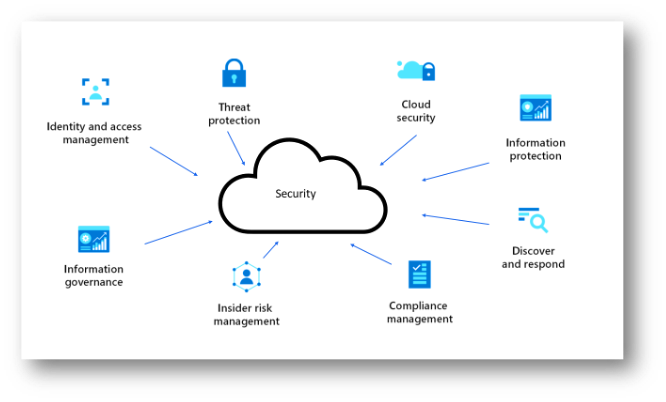
Our Services
Our Cloud Security Strategy Services
Our Cloud Security Strategy Services are designed to help your organization develop a robust security strategy tailored to your cloud environment. With our state-of-the-art solutions, you can:
- Risk Assessment: Identify and assess potential security risks and vulnerabilities in your cloud infrastructure.
- Strategy Development: Collaborate with our experts to create a comprehensive and customized cloud security strategy aligned with your business objectives.
- Security Implementation: Implement robust security measures to protect your data, applications, and infrastructure in the cloud.
- Incident Response Planning: Develop a clear plan for responding to security incidents, ensuring a swift and effective response.
- Compliance and Governance: Address regulatory compliance and governance requirements to protect sensitive data and adhere to industry standards.
Key Features
- Risk Assessment: Thoroughly assess potential security risks and vulnerabilities in your cloud environment.
- Customized Strategy: Receive a tailored cloud security strategy that aligns with your unique business goals and cloud infrastructure.
- Robust Implementation: Implement comprehensive security measures, including encryption, access controls, and threat detection.
- Incident Response Planning: Develop a clear and effective incident response plan to mitigate security breaches.
- Compliance and Governance Focus: Prioritize data protection and regulatory adherence to ensure compliance with industry standards and data privacy laws.
Benefits of Cloud Security Strategy Services
- Data Protection: Safeguard your sensitive data from unauthorized access and data breaches.
- Threat Mitigation: Detect and mitigate security threats proactively, minimizing potential damage.
- Compliance Assurance: Ensure compliance with data protection regulations and industry-specific standards.
- Business Continuity: Be prepared to respond effectively to security incidents, reducing downtime and operational disruptions.
- Cost Savings: Invest in comprehensive security measures to prevent costly security breaches.
- Cloud Migration
- Infrastructure Optimization
- Security and Compliance
- Cloud Architecture Design
- Application Development and Modernization
- Cloud-native Adoption
- 24/7 Support and Monitoring
-
- E2E assessment, planning and migration of on-prem data centers to AWS.
- Minimize downtime and risks with our migration strategies.
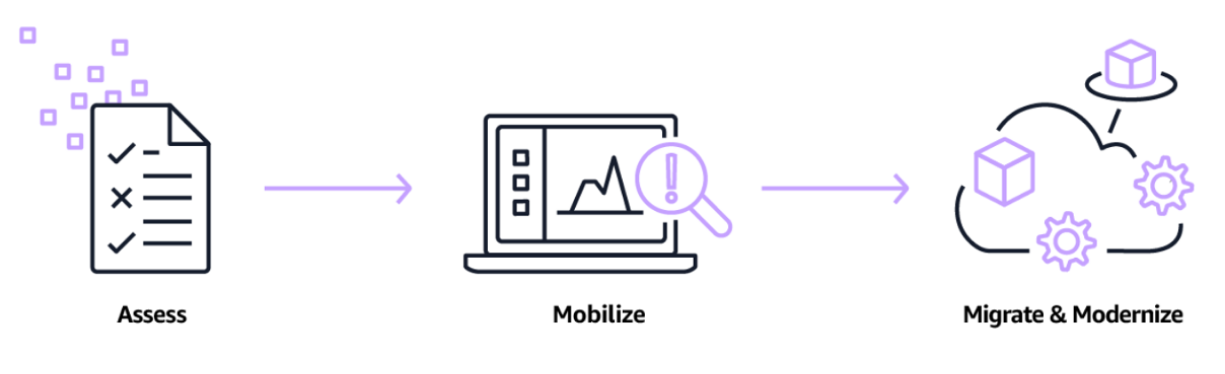
Our Approach

Supported Platforms
Cloud Success Stories: Real-World Insights
Discover how our cloud solutions have empowered businesses to reach new heights.Dive into real case studies showcasing the transformative power of the cloud.

Ready to start the
conversation?
We’re on your side, doing what it takes to get the job done right from the first consultation to your daily operations. Contact us for a free quote.
LET’S TALK
Fill out the form to be connected to one of our experts.


